As part of Seravo’s premium hosting and upkeep or WordPress sites, we take care of our customers’ data security: security updates as well as regular, automatic backups and tested updates. We also filter and restrict malicious traffic to sites. Our customers only need to practice good password hygiene – making sure that their own passwords are complex enough, and that they are used and stored correctly. The use of two-factor authentication is also strongly recommended.
On WordPress sites in Seravo’s upkeep, we have ensured that users will not be able to change their password, unless it is sufficiently complex and difficult to guess. Our systems also check that site administrators are not using a password that has been involved in a previous known security breach, and therefore cannot be found in leaked password databases. We also provide a tool called wp-check-passwords, which allows site administrators to check that no user on their site has a password that would be too easy to guess, such as having the same username and password.
Thanks to Seravo’s security measures, security breaches on our customers’ sites are rare. However, when they do occur, our statistics show that weak or leaked passwords are by far the most common cause. For this reason, we are updating our requirements and enforce using a strong password on the sites in our upkeep.
HTTPS Mandatory for All New Websites
Seravo’s upkeep has had HTTPS security as standard since its inception. Only good things can be said about using HTTPS. Not only does it protect passwords from spying among other things, but it also speeds up the website loading times: the new and faster HTTP/2 protocol only works with an HTTPS connection.
Vast majority (99%) of sites hosted by Seravo already use site-wide HTTPS security. Unfortunately, however, there is still a 1% of sites where the site administrator or developer has (usually accidentally) removed HTTPS protection from the site, either partially or completely. This is a risk to the security of the sites due to the risk of leaking usernames and login credentials.
For this reason, Seravo tightens password security so that HTTPS is always enabled on all new websites. This prevents users from ever logging in to their WordPress site with an unsecured connection, and at the same time sending their passwords over an unsecured connection. This also ensures that cookies, session IDs and similar keys are not sent without protection. This makes it much more difficult for potential attackers to hijack sessions or user IDs. As of late 2021, Seravo also forces HTTPS security on legacy sites. We hope that our customers will take into account in web development that those technical implementations that are in some way tied to using only an encrypted connection may therefore cease to work during 2021. Fortunately, there are likely to be very few such sites and implementations, as it is bad practice anyway. The reasons for not using encryption are usually related to third-party integrations that use outdated technology and do not support modern encryption methods.
Password Requirements on WordPress Sites at Seravo
Password checks on our customers’ WordPress sites are tightened as follows:
- User IDs with Editor or Admin privileges are checked upon login to ensure that the password is not found in the haveibeenpwnd database, the largest public collection of passwords leaked in past data breaches on the Internet. For other usernames, no check is performed.
- Our tool wp-check-passwords, previously only available from the command line, can now also be found in the WordPress control panel under Tools > Security. This makes it even easier to use the tool.
- In the security settings Seravo plugin, there is a new option “Disable XML-RPC completely” to completely disable the WordPress XML-RPC interface. This is an even more comprehensive option than Seravo’s existing options to block authenticated access via XML-RPC, as well as to block username iteration and login. Today, the use of the WP-JSON interface has almost completely replaced XML-RPC and is not required for most sites, although this feature is still enabled by default in the latest version of WordPress 5.6.
- All sites will have authenticated XML-RPC blocking enabled. Very few plugins or sites use this feature. The only common use is via Jetpack, which is explicitly enabled by IP addresses. Many clients already have this setting enabled, and now it’s only a matter of enabling it by default for all sites where it has not been explicitly disabled by the site administrator.
- All new WordPress sites provided by Seravo will have a WordPress Two-Factor plugin installed, which is likely to become part of the core WordPress experience in the future. This will make it easier for customers to become aware of its existence, and hopefully lower the threshold for its use.
- The Recaptcha plugin will also be installed on new sites in the future. This will lower the threshold for customers to use reCAPTCHA verification to prevent bots.
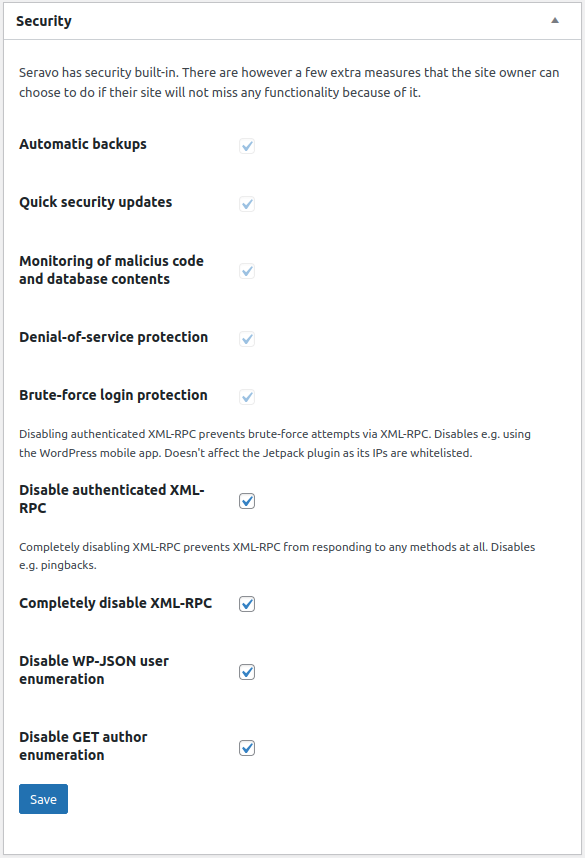
Some of the changes have been implemented in WordPress via the Seravo plugin.
The changes will take effect when the Seravo Plugin is next updated on the site.
On the left you see the options available to Seravo’s customers in the WordPress dashboard (wp-admin), Tools > Security menu.
Logs Reveal What’s Happening on Your Site
We also remind you that Seravo’s customers already have a number of security-related logs at their disposal:
wp-login.logcontains all logins, both successful and failedwp-user.logcontains all changes made to user IDs, for example, new users and changes to the access level of previous userswp-settings.logcontains changes made to the main settings of the sitewp-theme-security.logcontains the results of a security scan of the site’s current theme after updating the code files of the previous theme
Logs can be viewed from the command line in /data/log/ or in the WordPress control panel, under Tools > Logs. Seravo also has several command-line tools for displaying log summaries, such as wp-last-wp-logins and wp-last-ssh-logins. If there is reason to suspect that the currently used passwords are weak, you can use wp-reset-all-passwords command to reset all passwords for all WordPress users, forcing users to choose a new password. However, this should not be used without good reason, as it will cause extra work for site users.
Unfortunately Common: Weak Passwords
Seravo’s security protections are at an excellent level. Currently, the most common reason for data breaches on sites in Seravo’s upkeep is that the intruder simply logs in with a compromised password, which has been leaked in the past for a reason or another. If a user has the same password on WordPress as the one used on some compromised site, it is easy for an intruder to gain access by simply trying to log in with the same password found in a list of leaked passwords.
Our security protections monitor and restrict traffic to WordPress login pages, and outsiders cannot break into the site simply by attempting to guess the password of a user. If the password is very simple (for example, if it is in the top 100 most commonly used passwords), restricting logins is not enough, as an intruder can get in with just a few tries.
With these changes we improve the data security of your WordPress site. As this affects already existing security mechanisms, the update should not cause any additional inconvenience for our customers.

