We often hear questions about the Let’s Encrypt certificate that we offer as a part of all of our hosting plans. People tend to wonder how a free certificate can offer sufficient security and if Let’s Encrypt can really answer the needs of the customer, regardless of the size of their site or business.
In this article, we’ll shed some light on what Let’s Encrypt exactly is and why you don’t need an expensive certificate to be secure.
What is Let’s Encrypt?
To really dig into the Let’s Encrypt, we have to take a look at the group behind it, the Internet Security Research Group. ISRG is a public benefit corporation that was founded to serve as a home for public benefit digital infrastructure projects. The group founders and sponsors consist of some of the biggest names in information technology, such as Mozilla, EFF, Cisco, Akamai, Google, Facebook, and RedHat.
The first project of the group was the Let’s Encrypt Certificate Authority, which now secures more than 125 million websites all over the world.
For some perspective on the impact of Let’s Encrypt we can look at a few stats. Back in 2013, before the Let’s Encrypt CA, roughly 26% of the web pages loaded by Firefox were using a TLS Certificate. This year the same figure shows the percentage of pages loaded over HTTPS is about 78%. Let’s Encrypt issues current
How Does Let’s Encrypt Work?
The Let’s Encrypt Certificate Authority uses domain validation to make sure that the server requesting the certificate actually controls the domain for which the certificate is requested.
Domain validation – or DV for short – is a process that can be completed without any human intervention, which makes it very easy to automate and thus very cheap for the hosting companies such as Seravo to manage. In order to make sense of this all, let’s take a look at how the DV process actually works:
- Software on the web server requests a certificate from the Certificate Authority (in this case the request is sent to Let’s Encrypt Certificate Authority).
- The Certificate Authority uses a private key pair to uniquely identify the server asking for the certificate and then checks that the server has the control over the domain they wish to issue the certificate to.
- The web server then verifies that it indeed controls the domain to the Certificate Authority.
- Finally, the Certificate Authority makes a record of the validation and assigns it to the private key of the server for future requests.
After this authorized key pair has been formed, it’s simple to request, renew, and revoke certificates. The web server can send the requests to the Certificate Authority with its authorized key. Once the Certificate Authority has verified the key, the web server
Renewing or revoking certificates is a similar process. The web server sends out a request for the renewal or revoking of its issued certificate along with its public key. The CA verifies the key and completes the request.
If you’d like a more in-depth look at the process, check out Let’s Encrypt’s documentation.
Because all this can be done without any human intervention, the entire process can be automated. This saves us the work and thus the cost of manual certificate requests and renewals, which are required with other types of certificates. This is
EV, OV, DV – What are the differences?
A domain-validated (DV) certificate is not the only kind of certificate available to websites. There are also certificates with organization validation (OV) and extended validation (EV). All of these certificates use the same technology and the same cryptographic algorithms for the encryption of traffic. The key differences are the validation of the ownership and certificate issuing.
While the domain validation process can be completely automated and completed without any human intervention, the opposite is true for both EV and OV certificates. Both require additional verification from the owner of the site requesting the certificate, usually in the form of documents that prove the identity of the person and the existence of the business or the company requesting the certification.
The extra verification is often used as a sales argument for OV and EV certificates. The additional steps can seem to add a layer of trust to the certificate, but there is not much support to back up these claims.
Let’s have a look at how this added layer of security is supposed to work. Outside of the validation process, the biggest difference in EV certificates to DV certificates is that they add the name of the business entity controlling the certificate to a green bar next to the padlock icon in the address bar of the browser. DV and OV

The idea here is that the visitor can verify that the site belongs to the business they intend to use and is not maliciously attempting to phish their credentials. While this might sound good on paper, it’s not all that simple, as such security mechanisms place the burden of authentication on the user instead of the system.
Another issue this approach has is that the way browsers display these certificates keeps changing over time. The padlock icon is already on it’s way out and there
The final major difference between a DV certificate offered by Let’s Encrypt and a typical EV certificate is the expiration interval. All certificates issued by Let’s Encrypt expire in 90 days, whereas EV certificates are typically issued for much longer periods, even for up to two years at once.
Considering the lengthy and cumbersome process that is required to get an EV certificate in the first place, the long expiration time may seem like a good thing. Again, it’s not that straight forward in reality. The renewal process is no simpler than the original request and with no way to automate the renewal process, this can easily lead to expired certificates.
This means that your site could look like this until the complicated renewal process is complete, which is not something any business would like:
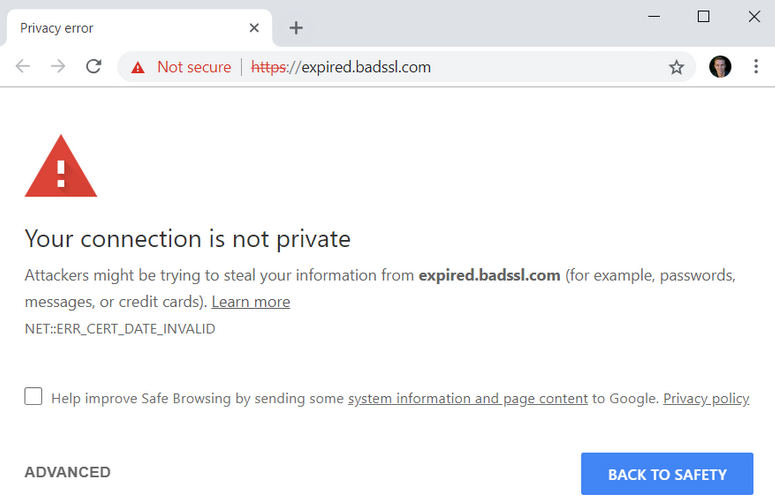
Let’s Encrypt’s automated renewal process makes it easy to avoid such scenarios. The shorter expiration is also beneficial in case the certificate key gets compromised, especially since the certificate revocation can’t blindly be relied on yet either.
It’s also good to consider that some of the biggest sites in the world such as Google, YouTube, Facebook, Amazon don’t use EV certificates, as it doesn’t provide any real additional security. So if you’re wondering whether your site or business should use an EV certificate instead of the Let’s Encrypt’s DV certificate, it’s most likely not worth the cost.
Why Use Let’s Encrypt?
The simplest answer would be that because it saves you all the headache of setting up the certificate, installing it correctly and handling the renewals in time, at no extra cost.
All Seravo hosted sites come with the Let’s Encrypt certificate installed automatically. As we explained, the whole process can be automated so there is no risk of your certificate expiring and you losing potential visitors to your site.
We don’t recommend using certificates from other sources. Should you still wish to use some other certificate for your site, or if your company policy requires a specific certificate, we do offer those as well. Check out our Plans for details.
We are also always keeping up with the latest technologies to ensure that our customers can sleep at ease with their sites running safely. We are currently working towards bringing the wildcard support to our customers, which is fully implemented in the Let’s Encrypt certificates.
Let’s Encrypt is not just sufficient. With the automated setup, zero cost and solid backing from the industry leaders, it’s more than enough for all sites – large and small alike. As Seravo’s customer, you will get it at no cost and no hassle to all your sites!


Comments
One response to “Why Let’s Encrypt is Enough”
Excellent article! I’ve had so much pain renewing certicates for clients using paid certificates. Nowadays naturally using Let’s Encrypt only.